How Enterprises Build Trust With Video Streaming..
DRM, short for “Digital Rights Management”, is anti-piracy technology. DRM is nothing new in the software industry. In fact, you may have even been using it in the 80s when you were booting up some of those DOS games.
With the growth of digital media, over-the-top content (OTT) and conversion technologies, the need for DRM has vastly increased. It has become easier for consumers to convert or ‘rip’ media. The popularity of peer-to-peer file sharing tools and applications like Popcorn Time have also created copyright challenges for content creators. It has made unauthorized distribution of copyrighted digital media much easier.
Digital rights management (DRM) exists, mainly, to keep content safe and minimize piracy. Some content owners require it. In the process, it can be a cumbersome beast that often hinders legitimate buyers from full use of the product in question.
DRM is used by content owners to control who gets to access their videos. It is particularly important for companies concerned with copyrights, namely the music and movie industries, who are partly or wholly dependent on the revenue generated from their work.
DRM is costly to implement so mostly the premium content providers use it. Ever try to watch a video from an OTT platforms like Netflix, Hulu, Disney or Amazon and it says that you don’t have access to it and need to upgrade your subscription? They are doing that with a DRM standard to protect those video assets.
DRM works in many ways, depending on the medium and the types of restrictions the publisher wishes to impose.
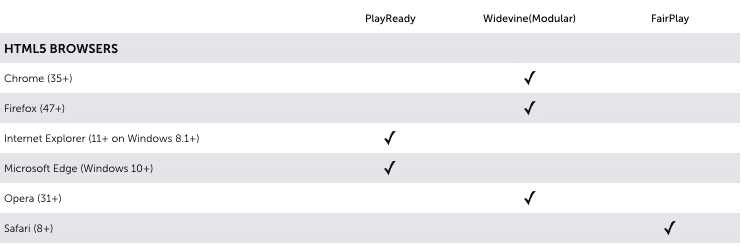
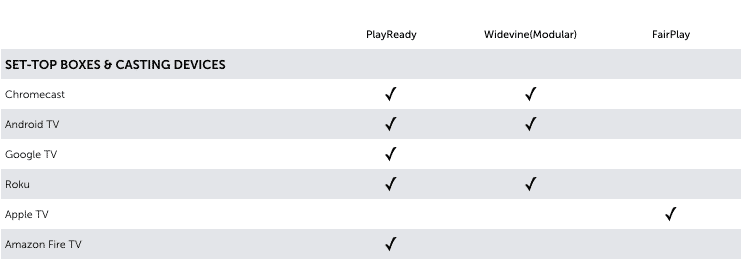
When selecting the ideal DRM converter for your needs, one thing that is critical is choosing a content protection solution that supports a range of consumer devices your target audience is using. Each DRM protocol has its own priority of consumer platforms. If you are distributing Hollywood content then you will be using at least one of these major DRM technologies:
Google Widevine (Modular)
The Widevine Modular system is broadly supported today in Chrome web browsers and Android devices. Widevine Modular can be deployed on the web with MPEG-DASH with CENC, using the same renditions, encrypted with the same AES-128 in CTR mode, or CBC mode, and packaged in the same fragmented MP4 containers as Microsoft PlayReady, making them broadly compatible.
Microsoft PlayReady
Microsoft’s PlayReady DRM is one of the most widely implemented DRM technologies, supporting MPEG-DASH with AES-128 in CTR mode and Microsoft Smooth Streaming to web environments and many Smart TVs and web-enabled connected devices.
Apple FairPlay
FairPlay is only supported in Apple products, requires a direct relationship with Apple as a registered developer, and can only be used for streaming HLS video. FairPlay uses the AES-128 encryption algorithm in CBC mode, either in MPEG2 Transport Stream, or more recently, fragmented MP4 containers.
If you want to achieve maximum device reach it’s impossible to use just one DRM. You need to use multiple DRM’s in parallel. The DRM-matrix below will give you more insight in what kind of DRM is needed per device and platform.

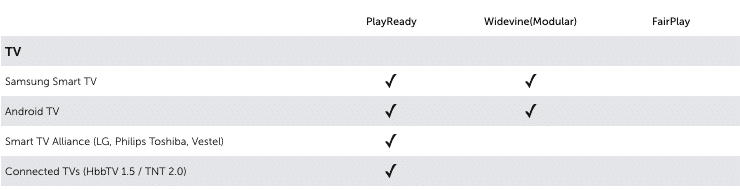
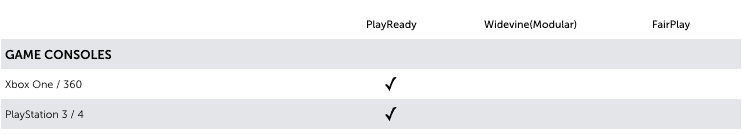
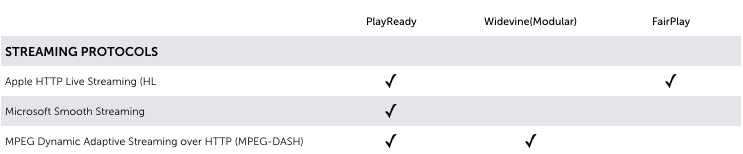
For people with some years of computer experience it is not hard to rip video content. There will always ways to bypass DRM. An example is the analog hole. The analog hole is a fundamental and inevitable vulnerability in copy protection. Regardless of any digital copy control mechanisms, if sound can be heard by an ear, it can also be recorded by a microphone. And if video, can be seen by the eye, it can also be recorded by a camera (or a screencast).
DRM makes it harder for lets say 80% of the people to illegally copy or access your video content.
Working with DRM to protect your valuable video assets can be a costly and time-consuming task, especially with the multitude of different DRM systems and user platforms on the market.
When considering video content protection there is a delicate balance between strength of protection and the barriers it presents in reaching the viewers. Always keep a good balance between difficulty of piracy and ease of purchase.
When implementing a video DRM strategy you should first check which content protection the content owner accepts. Does your OTT-TV proposition really need DRM? If you are distributing Hollywood content you do. But is you don’t maybe a lightweight solution like tokenized video delivery can be sufficient to secure your content and then you won’t have to go through all the hassle.
If you need any advice on selection the right way of protecting your valuable video content with DRM. Please contact us.
We can handle your video-on-demand and live protection so you can focus on getting content to market.
Please contact one of our online video experts. We’d be happy to give you personal advice about how you can get the most out of your video content.